
Early this week, news broke from security researcher, Jonathan Leitschuh he had discovered a vulnerability in Zoom that allowed unauthorized access to as many as 4 million webcams of Zoom users on Mac OS by simply getting a user to click on a link. These links are the standard (and delightfully simple) links that allow any user to easily join a Zoom meeting. Often looking like this (https://zoom.us/j/492468757). What was even more alarming was the fact that even those that have removed Zoom’s application from their system were still vulnerable due to a local host server that would reinstall the application upon the click of the link.
In Leitschuh’s artcle this morning, published on his Medium page, he discloses the depths of the vulnerability as well as his efforts to work with both Zoom and the browser providers Chrome and Mozilla that ubiquitously run the Zoom platform. The sub-header, raising alarm bells (as it should).
A vulnerability in the Mac Zoom Client allows any malicious website to enable your camera without your permission. The flaw potentially exposes up to 750,000 companies around the world that use Zoom to conduct day-to-day business.
To read the entire report on Medium
Note: The comments are as interesting as the research as other researchers and hackers weighed in on what they were finding in their exploratory sessions with the application.
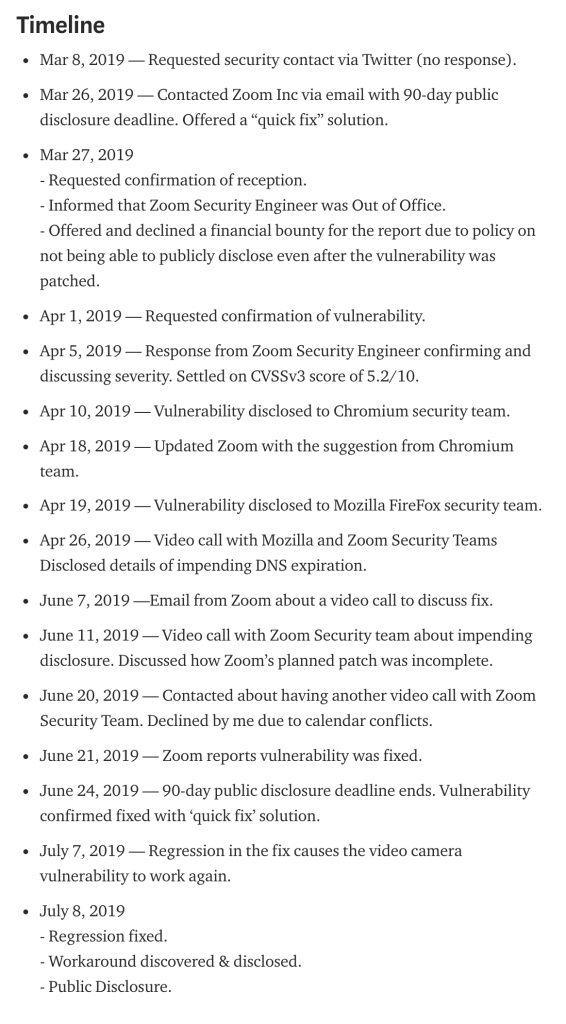
Analyst Take: Where to begin…This entire Zero Day vulnerability situation is a disaster and Zoom is somewhat lucky that they weren’t required to disclose this just prior to their IPO in April. Looking at Leitschuh’s timeline, he discovered the security flaw in March and the timeline dragged out for now more than 4 months without a permanent fix. The fact that all of this was happening during the period of the IPO rings alarm bells, especially the notation that the company chose only to apply a “Quick Fix,” which they later marked as a legitimate Fix, which then rolled back, but not until after the IPO. Of course, any connection between delaying efforts to fix and or disclose this vulnerability and the IPO are pure speculation, but the timing is really suspicious to me. On medium, the following timeline was posted:
In terms of the user experience of Zoom, I have been bullish. However, I have been raising alarm bells about the security of many bespoke collaboration applications. Slack, at one point faced serious push back after disclosing users favorite emoji’s, this of course meant that the company was able to read user messages (note: this is also because Slack messages aren’t end-to-end encrypted). Internal misuse, in this case, would seem to be an easier fix than the Zero Day vulnerability that Zoom is dealing with. I’m genuinely concerned about the company’s handling of the situation and the slow response they had in fixing the response during the allotted 90 day disclosure period. Perhaps even more ironic was the company somehow being able to finalize and offer a “Permanent Fix” just hours after the blog disclosing everything was published. Based on their quick fix of the issue today, it would appear to me that the company could have implemented a permanent fix more quickly, but they didn’t want to. This likely has to do with implications that would access less user data by turning off the camera natively.
My concerns also extend to the forced usage of the application that is causing the proliferation of users that only access the application due to an invitation. The way Zoom was setup (and this is common with many collaboration platforms), is that when you choose to join a meeting, any meeting you are invited to, you click the link and wind up downloading the application. Even if you only join a single meeting as a guest, you have downloaded the application and you now have the local host server on your machine that doesn’t fully rid you of the app even upon uninstalling it. The value to Zoom of this methodology is tremendous, but it is invasive as most users wouldn’t remove the application, and now they are potentially exposed to the vulnerabilities.
Given that there haven’t been any major breaches reported as a result of this finding, I don’t believe this is Armageddon for Zoom. However, this should be a significant warning that user experience and security cannot be mutually exclusive. The more Zoom is touting their enterprise capabilities the more they have to be steadfast in making sure that their users and their data (cameras and audio) are secure. I believe this is where collaboration tool providers like Cisco and Microsoft have a healthy advantage with their trust and competency in physical and software security. Now the aforementioned timing around the IPO with this entire debacle, I would really have loved to be a fly on the wall as this was happening. Oh, and don’t forget to put some tape on those webcams. It’s a sure fix to any video snooping that may take place on your device.
The original version of this article was first published on Futurum Research.
Daniel Newman is the Principal Analyst of Futurum Research and the CEO of Broadsuite Media Group. Living his life at the intersection of people and technology, Daniel works with the world’s largest technology brands exploring Digital Transformation and how it is influencing the enterprise. From Big Data to IoT to Cloud Computing, Newman makes the connections between business, people and tech that are required for companies to benefit most from their technology projects, which leads to his ideas regularly being cited in CIO.Com, CIO Review and hundreds of other sites across the world. A 5x Best Selling Author including his most recent “Building Dragons: Digital Transformation in the Experience Economy,” Daniel is also a Forbes, Entrepreneur and Huffington Post Contributor. MBA and Graduate Adjunct Professor, Daniel Newman is a Chicago Native and his speaking takes him around the world each year as he shares his vision of the role technology will play in our future.

