
What a time to be alive! The rapid advances of technology and dawn of an era dominated by the Internet of Things (IoT) has changed pretty much everything about life as we know it. Which is why it’s no surprise that cybersecurity is perhaps the greatest challenge CISOs face today.
But let’s back up. Why is the IoT such a big deal? That’s an easy one. The IoT essentially describes connected things. Smart TVs, cars, speakers, doorbells, lights, toys, sprinkler systems, refrigerators, surgical tools, cows, manufacturing facilities, utilities—there are millions of things connected to the internet, and millions more to come. In fact, it’s predicted that IoT devices will outnumber humans 4-to-1 by 2020—a mere two years away. That’s some serious growth, which is both good and bad. And it’s also why cybersecurity is, without question, the greatest challenge CISOs face.
As the Internet of Things becomes more pervasive and more and more things are connected, security and the added security-related responsibilities that are part of a CISO’s job become infinitely more challenging. We’re not talking hacked cellphones and phony Instagram accounts here. We’re talking, hacked utilities, self-driving automobiles, or cardiac monitoring machines, where lives could well be at risk.
Why is Cybersecurity the Greatest Challenge CISOs face?
So, why is cybersecurity considered the greatest challenge CISOs face today? For starters, cybersecurity today is infinitely more complicated than ever before. In addition, the business of hacking is booming right alongside, and whether motivated by money or power, or both, there’s no reason to expect that to abate anytime soon. Or ever.
The rapidly escalating number of connected things is one reason for the complexity of today’s CISO’s responsibilities. Another factor impacting and challenging CISOs is that it is not uncommon for developers to develop “cool” things without building security into the very foundation of whatever it is they’re developing, so it’s not uncommon to adopt some new piece of connected technology into operations, only to find that it’s not secure and/or easily hacked.
Connected things make attractive targets for hackers. We’ve seen instances of hackers taking control of cars, and hackers targeting computer control operators of U.S. energy facilities and hospitals. In May of 2017, a worldwide cyberattack by ransomware called WannaCry resulted in the shutdown of 65 hospitals in the UK, affecting MRI machines, storage refrigerators, and computers and impacted hospitals and healthcare facilities the world over.
It used to be that a CISO’s primary worry was the protection of data being stolen or compromised in some way. Now, in addition to protecting data, CISOs much also embrace continuous learning and make sure they stay ahead of the game as it relates to protecting people, devices, and machinery that, if hacked, could have disastrous and fatal consequences. Not only does this add pressure to the role, but also serves as one of the greatest challenge CISOs face.
The Rise and Risks of Ransomware
The rise of ransomware is a massive challenge CISOs face today, as mentioned above with a nod to WannaCry. The healthcare industry is especially attractive to hackers, and chances are good there are many healthcare CISOs who don’t sleep well at night wondering when the next attack will come. Healthcare ransomware attacks soared in the third quarter of 2017, eclipsing all other cyberattacks. Want more on that, check out Proofpoint’s 2018 Healthcare Threat Report.
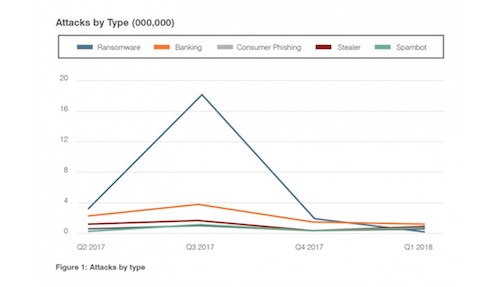
Ransomware is one of the biggest cyber threats that businesses, governments, and individuals face at the moment and also one of the greatest challenge CISOs face.
I wrote an article on this topic last year: 50 Percent of Businesses Report Ransomware Attacks in the Past Year, exploring data from both Sentinel One’s Global Ransomware Study and Symatec’s Ransomware and Business 2016 report. At that point in time, it was estimated that more than 50 percent of businesses were affected by ransomware hacks or had experienced security breaches, in just one year’s time. And that wasn’t just small businesses. It was businesses of all sizes. For example, CyberScoop reported in September of 2017 that FedEx reported a $300 million loss in first quarter 2018 to the NotPetya ransomware attack that impacted its European operations the prior year. This loss wasn’t from paying ransomware demands but from the cost of disaster recovery and system downtimes that occurred as a result. $300 million—that’s no small number!
Can Ransomware Be Life-Threatening?
So, can ransomware be life threatening? The fact that the healthcare verticals are especially attractive to cybercriminals makes that answer a resounding yes. The worst ransomware attack to date is the WannaCry attack, which paralyzed the UK’s National Health Service. It affected over 300,000 organizations worldwide, holding them ransom. However, in that case, no lives were at risk. That said, the hackers’ ability to cripple the NHS and block them from viewing patients’ files may have only been the beginning. The security breach to a national health service showcased that cybercriminals and terrorists can infiltrate hospitals and potentially access critical health devices on a hospital system. Software vulnerabilities, phishing attacks, internal risks, and third-party vendor systems all play a role here.
On a different front, given the fact that Russian hackers are reportedly targeting the energy sector with a specific focus on infiltrating and surveilling critical U.S. infrastructure, including energy and nuclear power plants, I’d say the chances of a ‘win’ there being potentially life-threatening are equally as worrisome. So ransomware is dangerous, for sure, and there’s every chance it could potentially be used in a way that would be life-threatening. It’s also one of the greatest challenge CISOs face.
What Risks Does a BYOD Culture Present?
In addition to ransomware, challenges for CISOs also include the risks that a Bring Your Own Device (BYOD) culture presents. With a rise in modern technology in the workplace, it is not at all uncommon for companies to employees to bring their own devices to work, instead of or in addition to company-provided devices. A BYOD culture, while inevitable, brings with it complicated headaches and a new set of challenges for CISOs and IT departments. The reality of BYOD being standard operating procedure in companies of all sizes is influencing security policies at organizations as they can potentially expose the whole organization to massive security risks.
Think that the ‘fix’ is simple: Perhaps a policy that specifies no personal devices at work? Let’s think about that for a minute. Here’s an example: My husband has two mobile devices, one for work and one for personal use. He conducts work on the business device regularly and tries to keep the personal phone strictly personal. But what happens when one day his work device is out of battery, he’s on the road, and has to access an important file, document, or piece of information. What does he do? Well of course he uses his personal mobile device. Multiply this times hundreds of thousands of employees across hundreds of thousands of instances and you can likely see the potential risk.
Employees unwittingly expose their companies to risk on a daily basis simply by opening emails and potentially clicking on phishing links, entering personal information where prompted, and BOOM — hackers win.
Here are just a few things that challenge CISOs (and keep them up at night) as it relates to a BYOD culture:
- Increased risk of data leakage — A mobile device is a network’s weakest link and prone to attacks. Mobile access to organization data can increase the risk of data leakage.
- Increased risk of malware — Employees can unknowingly install malware on their personal devices that can spread to the organization’s network.
- Higher exposure vulnerabilities — If employees download unsecure applications or operate on public networks, corporate data may be vulnerable to exposure.
- Combined personal data with corporate data — Lost devices containing both personal and corporate data, can be accessed by external parties.
A BYOD culture requires many things of a CISO and his or her IT team including a potential expansion on IT infrastructure, the development of more stringent cybersecurity policies, and engage in regular and frequent employee security training.
Cybersecurity Takes the Cake as a a CISOs Greatest Challenge
Today’s CISO is more critical to business operations than ever before and cybersecurity is, by far, a CISOs greatest challenge. CISOs have much responsibility. They are charged with keeping the companies they work for and the data that powers those companies safe and operational and accessible at all times. They are charged with keeping their customers and their data safe, and they are are counted on to protect against any and all kinds of malfeasance.
The role of a CISO is constantly evolving and becoming more sophisticated as technology continues to advance and dominate our world. It’s no wonder CISOs are highly sought after in the IT job market, as are other security-related IT talent. One of the biggest issues that organizations are facing is that they simply can’t fill vacant cybersecurity roles. ESecurity Planet predicts that some two million cybersecurity positions will remain unfiled by the end of 2018, which is causing CISOs and security teams to rely on Machine Learning and AI to combat cybercrimes. But when it comes to the nuts and bolts, human input is still required to make critical decisions, making the global skills shortage in cybersecurity one of the greatest challenge CISOs face in 2018. One challenge that may not be conquered.
So how do you keep up with it all? The clear challenge for CISOs is multifaceted. Today’s CISOs must embrace continual learning, and they must always be on the lookout for threats and vulnerabilities, whether posed by the IOT and connected devices, ransomware threats, BYOD, phishing attacks, and more. Vigilance requires the conducting of regular system checks, frequent device audits, development of robust disaster recovery plans, exploration of managed service solutions where applicable, and exploring offerings like colocation and whether they can provide some much-needed protection and security assurances. A CISO role is a big job. It’s an exciting job—and it’s a business critical job.
Other articles on this topic:
The Expanding Role of the CISO: Seven Attributes of a Successful Security Leader
Are Sophisticated Cybercrimes a Myth?
DHS, FBI say Russian hackers are targeting the energy sector
The original version of this article was first published on Futurum.
Shelly Kramer is a Principal Analyst and Founding Partner at Futurum Research. A serial entrepreneur with a technology centric focus, she has worked alongside some of the world’s largest brands to embrace disruption and spur innovation, understand and address the realities of the connected customer, and help navigate the process of digital transformation. She brings 20 years' experience as a brand strategist to her work at Futurum, and has deep experience helping global companies with marketing challenges, GTM strategies, messaging development, and driving strategy and digital transformation for B2B brands across multiple verticals. Shelly's coverage areas include Collaboration/CX/SaaS, platforms, ESG, and Cybersecurity, as well as topics and trends related to the Future of Work, the transformation of the workplace and how people and technology are driving that transformation. A transplanted New Yorker, she has learned to love life in the Midwest, and has firsthand experience that some of the most innovative minds and most successful companies in the world also happen to live in “flyover country.”

