
The News: Accenture was hit by a LockBit ransomware attack, which the company confirmed in a statement published late Wednesday morning. Accenture has claimed the attack is contained, but security experts are not quite so certain. Read more at Reuters.
Accenture Falls Victim to Ransomware Attack Following Report of Increase in …. Ransomware
Analyst Take: The news of the week on the cybersecurity front is that Accenture has fallen victim to a ransomware attack perpetrated by ransomware-as-a-service (RaaS) threat actor LockBit. What’s especially ironic here is that Accenture just last week published a report showing a 125% growth in the volume of cyber-intrusion activity globally, attributing the increased cyberattacks to web shell activity, ransomware incidents, and supply chain attacks.
According to its 2020 annual report, Accenture is one of the world’s largest tech consultancy firms, with some 560,000+ employees across 50 countries. The company’s client base spans industries the world over, including 91 Fortune 100 companies and 75% of the Fortune 500, with a client list that includes the likes of Cisco, Alibaba, and Google, to name just a few. IT services, operations technology, cloud services, technology implementation and consulting are just some of the many services Accenture provides.
It is no surprise to see Accenture targeted in this latest ransomware attack. ‘Go big or go home’ seems to be the rallying cry for threat actors these days, and Accenture is no doubt a big target.
Following the recent Kaseya ransomware attack, perpetrated by REvil, managed services providers have been in the sights of threat actors looking for easy targets that net big pay days. Kaseya provides IT solutions, including Kaseya VSA, which provides unified remote monitoring and endpoint management, helping IT teams deliver better service and operate more efficiently. The Kaseya attack was a supply chain ransomware attack that leveraged vulnerabilities in the Kaseya VSA software, upon which many managed services providers (MSPs) relied. While there are a whole lot of small to midsized managed services providers, there are also some very large ones — companies who offer cloud versions of specialty software and who provide specialty consulting services to specific industries. These managed services providers most often serve the small to midsize customer base — providing a much-needed assist when it comes to highly skilled IT services, as well as compliance and security services. And Accenture? Accenture, a publicly traded IT consultancy, is one of those very large managed services providers. In fact, on CRN’s Solution Provider 500 list for 2021, Accenture ranks #1.
Why Managed Services Providers Are Lucrative Targets
Why are managed services providers such lucrative targets? They are so attractive to threat actors because they have access to ALL of their customers’ businesses, and usually in the most crucial areas — like their data and their networks. MSPs are highly trusted vendor partners and a logical target for cyber criminals. The Kaseya attack was announced on July 2nd. By July 22nd, the company announced that a universal decryption key had been developed, circumventing the ransom demands. This followed a July 9th conversation between U.S. President Joe Biden and Russian President Vladimir Putin where Biden told the Russian leader that he must “take action” against cybercriminals acting in his country and warning of future action on the part of the U.S. if Putin failed to act. While there’s speculation that Putin might in some way have aided in the Kaseya situation, chances are good that there were already numerous MSP-directed attacks already underway.
Just a few weeks after the Kaseya attack, the Cybersecurity and Infrastructure Security Agency (CISA), who serves as the nation’s risk advisor, addressed the very real threat for MSPS, publishing guidelines for MSPs and small and mid-sized businesses. The CISA guidance advised against the dangers cyber threat actors, particularly state-sponsored advanced persistent threat (APT) actors, pose to MSPS and their customers and provided guidance on mitigations and hardening guidance.
The Accenture LockBit Ransomware Attack
While the Kaseya attack was perpetrated by the REvil gang, the Accenture attack came at the hands of a group known as LockBit 20. Like REvil and DarkSide (responsible for the Colonial Pipeline cyberattack), LockBit is a Ransomware-as-a-Service operation. LockBit uses an affiliate model to rent out its ransomware platform, monetizing it by taking a cut of any ransom payments.
Reports from Cyble, a dark web and cybercrime monitoring firm, indicate that LockBit demanded $50 million from Accenture in exchange for 6 TB of data. Accenture issued a statement on Wednesday, claiming that the company had quicky identified the intrusion into ‘one’ of its environments and that the incident and been completely contained, with impacted servers isolated.
Also on Wednesday, VX-Underground, claiming to be the “largest collection of malware source code, samples, and papers on the Internet” tweeted something slightly different: .@Accenture “Through our security controls and protocols, we identified irregular activity in one of our environments. We immediately contained the matter and isolated the effected servers …
After 6TB of data was exfiltrated – 2,500 employees, 37,88 machines compromised.

Image Credit: Twitter
Cybereason’s Tony Bradley has shared the LockBit gang appears to be on a hiring spree, based on wallpapers displayed on compromised systems that invite insiders to help, and promising lucrative payouts to folks who do. This recruiting of corporate insiders was covered recently by Bleeping Computer’s Lawrence Abrams, and is thought to perhaps be a move to cut out the middlemen in the ransomware-as-a-service operation that has become so prevalent, and set up threat actors perpetrating the hacks to keep more of the profit.
Comments from Cyble researchers on Twitter indicate the possibility that the Accenture hack was perhaps an inside job. Cyble claims that LockBit has been hiring corporate employees to gain access to their targets’ networks and there are rumblings that this hack is an inside job, by someone who is still employed at Accenture — but Cyble stated on Twitter that there’s doubt of that actually being the case.
One thing is certain — hackers are very good at what they do, they are excellent at picking lucrative targets, and once they ‘getcha’ they want to let everybody know how easy it actually was. Bradley shared that the LockBit group revealed the attack on their site on the DarkWeb in this way —
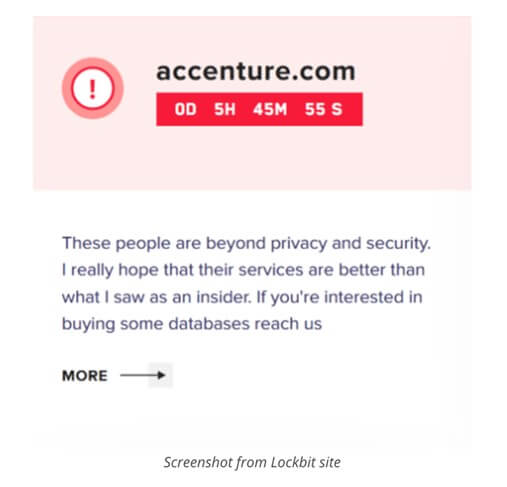
Image Credit: Cybereason
Nice burn.
The Problem With a Hack When You’re In the IT Security Business ….
Here’s the problem I have with the Accenture hack — the company should have known better. That’s harsh, but it’s reality. Companies this big, providing mission critical IT and security operations and consulting services on how to do things right — to clients the world over — cannot afford to have vulnerabilities that can be exploited. And these vulnerabilities weren’t a secret. LockBit threat actors are known to be actively exploiting vulnerabilities in the Fortinet FortiOS and FortiProxy products (CV#-2018-13379). That specific vulnerability, which is a path-traversal flaw in the SSL VPN, has been exploited numerous times over the last few years. The Australian Cyber Security Centre issued an advisory just last week warning that LockBit 2.0 ransomware attacks against Australian companies were accelerating, and also that these encryption attacks were combined with double-extortion attacks, which are threats to publish data. In the U.S., both the FBI and CISA have repeatedly warned that APT nation-state actors are actively exploiting this vulnerability to gain initial access within specific, targeted, networks.
Ransomware was already on Accenture’s radar screen, and it would be expected that the company would have stringent security access controls in place, protecting against any threats, including any insider threats.
In summary, this is another cyberattack, much like SolarWinds, and Kaseya, and the Microsoft Exchange Server attacks that came before, that we won’t have any real way of knowing the true extent of the damage for some time to come. I should also note that according to CyberScoop, and citing an internal memo, Accenture noticed the LockBit attack on July 30th. The statement from Accenture acknowledging the hack didn’t happen until August 11th — and I’m guessing the only real reason that acknowledgement happened is because security researchers noticed the posts from LockBit. Does GDPR play a role here? What obligations does a company like Accenture have to quickly acknowledge and report a security breach? I’m thinking these are questions we’ll be asking more of and this will most definitely be one security breach we’ll all be watching play out.
And a final word of warning, if you’re an Accenture customer, do your due diligence, now, on the security front. If you’re a managed services provider, shore up ALL your client operations, your security access controls, and make sure all patches are up-to-date at all times — because LockBit (and others) are coming for you.
Disclosure: Futurum Research is a research and advisory firm that engages or has engaged in research, analysis, and advisory services with many technology companies, including those mentioned in this article. The author does not hold any equity positions with any company mentioned in this article.
Other insights from Futurum Research:
What Does The Poly Network Hack Mean For DeFi
Bipartisan Lawmakers Work Toward Disclosure Bill For Cybersecurity Breaches
Image Credit: Mint
The original version of this article was first published on Futurum Research.
Shelly Kramer is a Principal Analyst and Founding Partner at Futurum Research. A serial entrepreneur with a technology centric focus, she has worked alongside some of the world’s largest brands to embrace disruption and spur innovation, understand and address the realities of the connected customer, and help navigate the process of digital transformation. She brings 20 years' experience as a brand strategist to her work at Futurum, and has deep experience helping global companies with marketing challenges, GTM strategies, messaging development, and driving strategy and digital transformation for B2B brands across multiple verticals. Shelly's coverage areas include Collaboration/CX/SaaS, platforms, ESG, and Cybersecurity, as well as topics and trends related to the Future of Work, the transformation of the workplace and how people and technology are driving that transformation. A transplanted New Yorker, she has learned to love life in the Midwest, and has firsthand experience that some of the most innovative minds and most successful companies in the world also happen to live in “flyover country.”

