According to the latest annual PwC survey of the Global State of Information Security, the number of cyber security incidents detected is rising sharply, while the amount spent on security has been falling. Given the extremely high cost of a cyberattack to a businesses’ reputation and day-to-day operations, it’s a bit of an understatement to say this might be considered a somewhat surprising development. And whether you’re an IT pro or a managed service provider delivering IT services to clients, security is likely something that’s high on your radar screen.
It’s not an understatement to say that these numbers illustrate just how much a sense of complacency has crept into the issue of IT security. And as you no doubt know, no business in any industry can afford to be complacent when it comes to cybersecurity today. That said, it’s time that some common myths and misconceptions about online security and data breaches were debunked.
But before we get to that, consider the PWC report headlines—and the size of these numbers—and you’ll get a feeling for the size of the challenge. Hopefully, the information here will also arm you with what you might need when it comes to discussions about budget allocations specific to security needs.
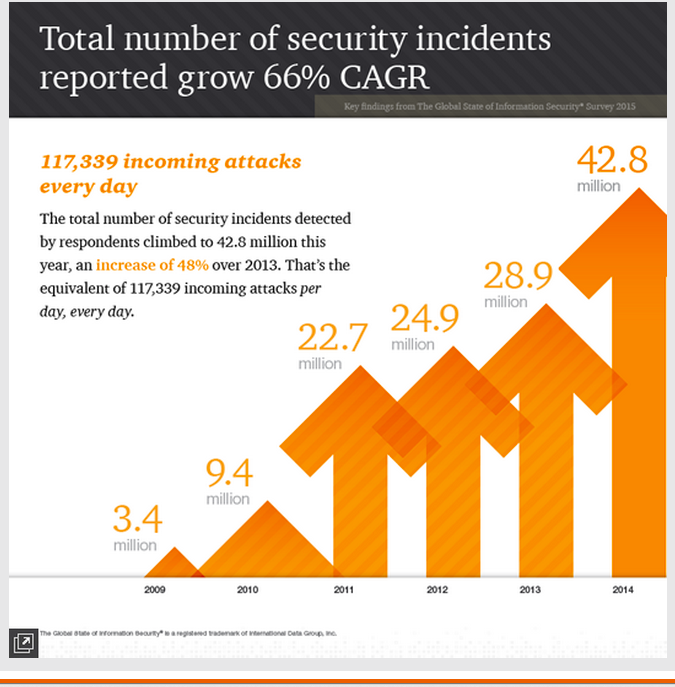
Security incidents are on the rise. The number of reported security incidents rose to more than 42 million in 2014, a 48 percent increase in one short year. In fact, the compound annual growth rate of incidents has grown by 66 percent, year over year since 2009.
Financial losses are high. The number of respondents reporting losses of $20 million or more was almost double than reported losses from the previous year. Ouch.
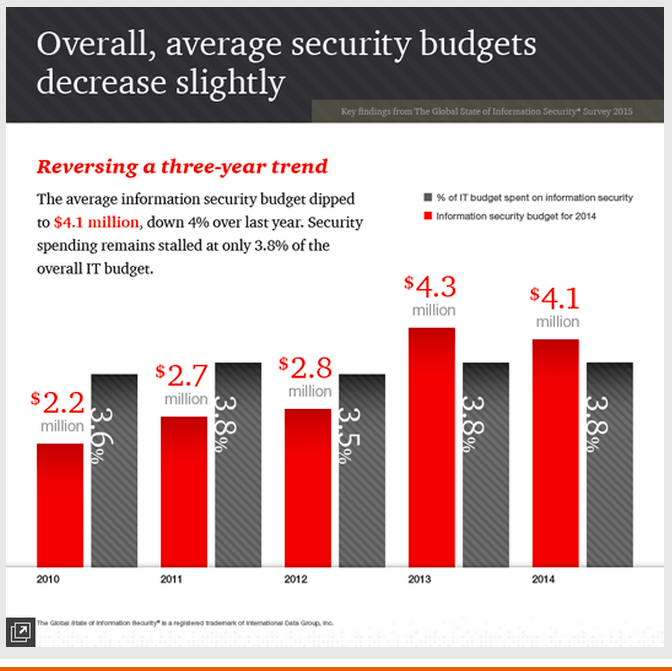
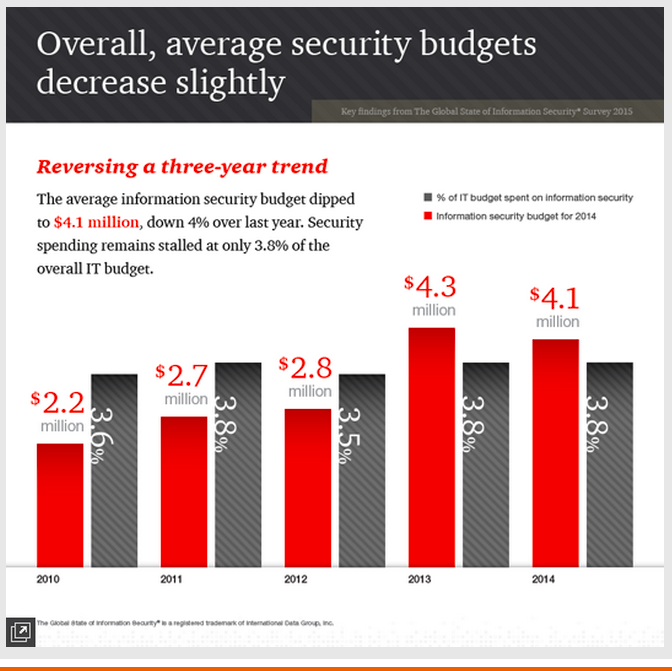
IT Security budgets are falling. Overall information security budgets fell by four percent in 2014 compared to the previous year. While larger and medium sized organizations showed a modest five percent increase in security spending, companies with revenue of less than $100 million more than compensated for that teeny increase by slashing their security budgets by an astonishing 20 percent.
Security spending not expected to rise. The percentage of security spending as a proportion of the overall IT budget remains low, and there are no signs that increases will be seen any time soon.
Statistics of this kind suggest that the corporate approach to cybersecurity leaves something to be desired, perhaps due to some dangerous misconceptions that have become ingrained in many organizations. This topic was the theme of a recent article from Michael R. Overly and Chanley T. Howell, partners at law firm Foley & Lardner and co-authors of a whitepaper on the subject of cybersecurity. They highlighted five “myths” around IT security that they think need to be dispelled in business organizations. Let’s take a look:
Myth #1 “It’s all about the data.”
Security is about more than just securing data to make sure unauthorized users can’t access it. A key element of IT security is also to protect the networks and systems that store and transmit said data against attack. A denial of service attack, designed to prevent legitimate users from accessing data, can be extremely damaging to an organization’s ability to even function, which, if you were, let’s say, a financial or healthcare institution, would cause widespread inconvenience (never mind potential panic) among your clients and customers. Say goodbye to your reputation in the process.
Myth #2 “It’s all about privacy.”
While protection of personal information is essential, the security of other information shouldn’t be overlooked. Sensitive business information such as financials, proprietary intellectual properties (e.g. trade secrets or source codes), pricing data, and other data that competitors would like to get their hands on should be equally protected.
Myth #3 “It’s all about confidentiality.”
Overly and Howell remind us that security is a lot more than just ensuring data can’t be accessed by the wrong people. To be truly secure, data management needs to follow the three tenets of “CIA”:
- Confidential—It must be protected from unauthorized access
- Integrity—It can be relied on as being accurate
- Availability—It can be accessed for legitimate use as and when required
Myth #4 To be a hacker you must be a technological genius.”
A dangerous assumption in the era of YouTube tutorials—when someone with limited technological knowhow can download tools, or view how-tos online to enable a hacking attack. Nor is it all about hacking these days. Social engineering and “phishing” techniques are also deployed so as to trap the unwary and find a way into unauthorized areas.
The PwC report highlights that respondents to the survey pointed to employees as the greatest cause of security incidents. The vast majority were no doubt acting without any intended malice, and it’s a known fact that human error does play a large role in many security mishaps. However, it also draws attention to the need for training to raise employee awareness of potential threats.
Myth #5 “I can achieve 100 percent security.”
The co-authoring attorneys point out that complete security is neither required by industry practices nor stipulated by law; businesses are only required to do what is “reasonable.” And, of course, while it may be possible in practice to secure systems 100 percent, the reality is that it would most likely make them totally unusable. As with everything, a balance between usability and effectiveness must always be struck.
Responses to the PwC study suggest that less than half of organizations have elevated responsibility for information security to board level, which is telling in and of itself. Cybersecurity needs to be top-of-mind for C-Suite executives and senior leaders, and this is something that your IT team and/or your managed service provider can (and should) work to bring about.
What do you think about the study results? Are these cyber security issues identified as real threats real issues or do you think they are overblown hype? What do you see as the greatest threats to companies? If you’re an MSP, do you think your clients fully understand the security threats facing their companies? I’d love to know your thoughts on this issue.
If you want to dive in further, the Managed Services Security team at IBM’s report, the IBM 2015 Cyber Security Intelligence Index, offers a really in-depth overview of the major threats to businesses worldwide over the course the the past year—definitely worth a read.
Additional Resources on this Topic:
The Five Biggest Cybersecurity Myths, Debunked
Debunking the Top Cloud Security Myths
Four Big Cyber Security Challenges (and How to Overcome Them)
This post was brought to you by IBM for MSPs and opinions are my own. To read more on this topic, visit IBM’s PivotPoint. Dedicated to providing valuable insight from industry thought leaders, PivotPoint offers expertise to help you develop, differentiate and scale your business.
photo credit: Cyber Security at MoD via photopin (license)
This article was originally seen on V3+Broadsuite Blog.
Shelly Kramer is a Principal Analyst and Founding Partner at Futurum Research. A serial entrepreneur with a technology centric focus, she has worked alongside some of the world’s largest brands to embrace disruption and spur innovation, understand and address the realities of the connected customer, and help navigate the process of digital transformation. She brings 20 years' experience as a brand strategist to her work at Futurum, and has deep experience helping global companies with marketing challenges, GTM strategies, messaging development, and driving strategy and digital transformation for B2B brands across multiple verticals. Shelly's coverage areas include Collaboration/CX/SaaS, platforms, ESG, and Cybersecurity, as well as topics and trends related to the Future of Work, the transformation of the workplace and how people and technology are driving that transformation. A transplanted New Yorker, she has learned to love life in the Midwest, and has firsthand experience that some of the most innovative minds and most successful companies in the world also happen to live in “flyover country.”