
The News: A Twitter hack this past week hit some of the platform’s most famous users has far-reaching meaning for CISOs and security vendors and the social network continues to piece together details on what actually happened. The basics: On Wednesday, July 15, 2020, a massive hack compromised 130 Twitter accounts and pretty much had the social media site at a standstill for hours. The accounts impacted during the Twitter hack included those of Bill Gates, Kanye West, Kim Kardashian West, Elon Musk, Joe Biden, Warren Buffet and others promoting the address of a bitcoin wallet with the claim that the amount of any payments made to the address would be doubled and sent back — a known cryptocurrency scam. The FBI is now investigating what might well be more than simply a troubling data breach, but instead, a targeted attack on the personal communications of some of the world’s most influential people. More on that from CNN Business.
What the Massive Twitter Hack Means for CISOs and Security Vendors
Analyst Take: The hack was subtle — at first. I noticed a Tweet by Elon Musk stating he felt generous during the COVID crisis and wanted to “give back.” Known for his quirky nature, I initially believed the tweet, but then it was soon revealed that his and other famous accounts had been hacked. As the Twitter hack has been investigated, it was revealed that the hacker leveraged an internal Twitter admin tool to gain access to high-profile accounts. In a few hours, Twitter tweeted that “a coordinated social engineering attack” on employees gave a hacker “access to internal systems and tools.”
To note for the digital history books, this is an impressive hack. Since its founding in 2006, this hack is unprecedented on Twitter. While these kinds of scams are common, to have such a number of high profile accounts be hacked simultaneously is not. According to TechCrunch, the main blockchain address used on the scam site had collected more than 12.5 bitcoin ($116,000) by the minute in a very short time.
As the FBI, cybersecurity investigators, lawmakers and Twitter employees continued to investigate this hack into the weekend, more details have come to light. It appears that young, relatively inexperienced hackers were at the heart of the attack — good news for those worried about a nation-state targeted attack. The bad news? Well, there are multiple parts to that one. First and foremost, this is a huge hit to Twitter’s credibility and the company took a $1.3 billion hit in premarket trading the following day as a result. Equally of concern, the investigations have shown that the hackers were able to fully download data from eight of those compromised Twitter accounts. This means that the hackers used the “Your Twitter Data” tool to download all data relating to those accounts, including their private messages. Twitter reported that none of those eight accounts were verified accounts but did not provide any further detail about this.
How They Did It (and Why CISOs Lose Sleep Over Hacks Like This)
How’d they do it? Largely by way of a coordinated social engineering attack. Social engineering is when users are manipulated, tricked, or convinced to hand over their access to a system. So, hackers don’t hack as much as trick people into giving up their security creditials.
While CISOs today are focused on modern tools that detect and mitigate malware, simultaneously they must also be aware of the behavior by hackers, especially on popular sites that are found on the Dark Web. The New York Times reports that logs from a messaging platform called Discord presented evidence that the hack was connected to four people whose social media accounts matched the cryptocurrency accounts involved in the hack. The central hacker went by the username Kirk and, according to an analysis of the Bitcoin transactions by The Times with assistance from the research firm Chainalysis, he was the hacker mainly responsible for taking money in and out of the same Bitcoin address.
As a prime example of criminal manipulation on the Dark Web, Kirk met corroborators like “lol” and “ever so anxious” on the website OGusers.com where hackers buy and sell social media screen names. Kirk asked “lol” and “ever so anxious” on Tuesday if they wanted to be his middlemen in selling Twitter accounts to the online underworld and proposed tthey would each take a cut from the transactions. In the midst of brokering Twitter accounts, Kirk also proved he had deep access to Twitter’s systems and sent out screen shots of the platform’s internal dashboard, while also demonstrating that he could quickly change fundamental security settings on any user name. Informants claim Kirk got access to Twitter credentials when he found a way into Twitter’s internal Slack messaging channel and conveniently found credentials posted in the channel (oops). He also got access to the company’s servers.
What started out as overtaking lesser-name Twitter accounts, selling highly sought after “OG” Twitter accounts with short names (e.g. @06), and other tomfoolery quickly escalated to taking control of celebrity accounts (mainly by Kirk) by 3:30 pm on Wednesday afternoon and the bitcoin links being tweeted. In an effort to mitigate risk, Twitter disabled the ability to send new tweets, largely for verified accounts, causing much uproar in the Twitterverse.
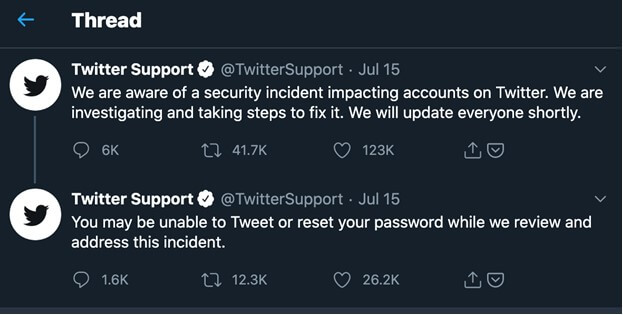
Twitter caught up with the scams, the accounts were finally shut down by 6:00 pm in the evening. Tweeting ability returned to mostly full functionality by about 9pm ET on Wednesday evening
While investigating the hack, researchers found the attackers had fully taken over the victims’ accounts and also changed the accounts’ email address making it harder for real users to gain access. A hack like this during this time of a global pandemic is not surprising. As I wrote about old malware making an IoT comeback back in March, it’s very typical for attacks to be on the rise during a time of crisis, and especially now as more people are losing jobs and looking for fast ways to make fast money. What’s impressive about this massive Twitter hack is that it was able to penetrate the administrative system of a major social media platform and attack major tech accounts such as Apple. In all, 130 accounts were targeted. The identity of Kirk, and how he was able to penetrate Twitter’s systems, remains unknown — for now anyway.
What’s Ahead for CISOs and Security Vendors
This massive Twitter hack proves that as much as security vendors tout they are able to stay ahead of the latest malware and cyber-attack methods, nothing is foolproof. It is crucial that CISOs and their teams have both technological capabilities and expertise that allow for real-time threat detection, dashboards that provide real-time SOC insights, the ability and expertise to provide immediate recovery, and that they are also staying on top of the goings-on on the Dark Web as much as possible. In addition, continuous evaluation of security protocols, credentialing, and frequent and regular employee training on all things related to social engineering are all needed in order to keep companies as secure as possible. Enterprise teams aren’t infallible or are vendors infallible, but if they both work together, cybersecurity protocols can be much improved. In this case, it appears to have even come down to a personnel issue, as in what level of employees had what type of secure or non-secure access, which apparently made these prominent accounts vulnerable. Such public attacks as this puts us all on guard and makes CISOs both more nervous and more important than ever. This is not the last of these very public attacks and companies will have to make sure they are prepared as they can be.
Futurum Research provides industry research and analysis. These columns are for educational purposes only and should not be considered in any way investment advice.
Other insights from the Futurum team:
What to do About Zoombombing as Hackers and Security Issues Plague Zoom
Failing IoT Security Means Old Malware Makes IoT Comeback
CISO’s Playbook for Leading Security During COVID-19 – Futurum Tech Podcast Interview Series
Image Credit: New York Post
The original version of this article was first published on Futurum Research.
Sarah brings 24 years of experience as an industry analyst to the Futurum team. She most recently served as the head of industry research for Oracle. Her experience working as a research director and analyst extends across multiple focus areas including AI, big data and analytics, cloud infrastructure and operations, OSS/BSS, customer experience, IoT, SDN/NFV, mobile enterprise, cable/MSO issues, and managed services. Sarah has also conducted primary research of the retail, banking, financial services, healthcare, higher ed, manufacturing, and insurance industries and her research has been cited by media such as Forbes, U.S. News & World Report, VentureBeat, ReCode, and various trade publications, such as eMarketer and The Financial Brand.

