As the number of threats and security breaches continue to grow, protecting your business from a cyber-attack takes a conscientious and sustained effort. Cybercriminals are expanding their forces and the assaults are becoming more sophisticated every day. If you aren’t fully engaged in your cyber security efforts you could be vulnerable. Do you know the biggest threats to your cyber security and how to fight them? The 2018 Verizon Data Breach Investigation Report (DBIR) has the answers.
2018 Verizon Data Breach Investigation Report: What Has Changed?
The 2018 Verizon Data Breach Investigation Report is based on research compiled using over 53,000 cybersecurity incidents and over 2,300 data breaches from 65 countries. Between last year and this year, various changes took place that can demonstrate the state of security presently.
In the 2018 Verizon Data Breach Investigation Report , 24 percent of victims were healthcare organizations, a 9 percent increase from last year’s percentage of 15 percent. A whopping 58 percent of all victims were categorized as small businesses this year, perhaps one of the most important changes in the climate.
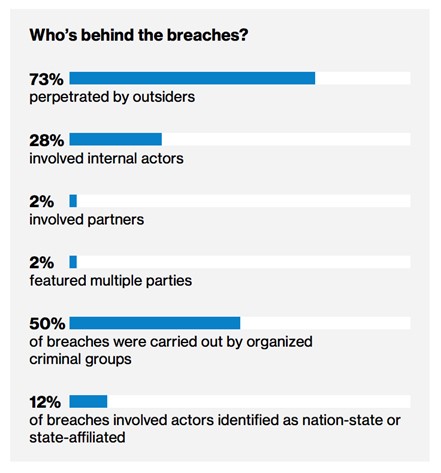
The biggest percentage of breaches are orchestrated by outsiders yet again in 2018, however, the percentage decreases to 73 percent compared to last year’s 75 percent. Hackers are continuing to evolve, this year utilizing pretexting to target HR departments, accounting for 170 incidents this year, a five time increase over 2017. Hacking is also the highest reporting form of data breaches yet again.
According to this year’s report, the top five industries suffering the most breaches include: healthcare, accommodation, public, retail, and finance.
It is critical that organizations, whether large or small, shift their focus to protecting all aspects of business, from the top to the bottom. This includes focusing on outside threats as well as inside threats, protecting employees from engaging in phishing and hacking scams through email and social and placing emphasis on the importance of protecting demographic information within the HR departments.
Motives and Tactics Behind the Attacks
There are many reasons behind the motivation of cyber criminals. However, this year and in previous years, it has been found that financial gain is the primary motivation behind data breaches and cybercrime. The second motive following financial gain is espionage. These two motives together made up for 90 percent of the breaches investigated.
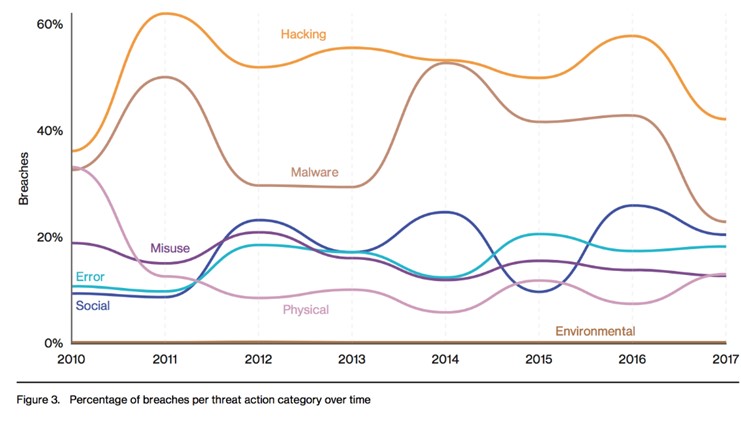
Most of the tactics were found to be hacking tactics, followed by malware. However, there should also be a focus on social hacking such as impersonation of an individual or a group attempting to receive pertinent information or credentials. Following social hacking is human error, physical hacking and misuse of information.
Leading Threat Actions and Patterns
This DBIR includes leading threat actions that are seen within the organizations that have experienced a data breach. These threat actions can show us patterns that enable us to see where cybercrime is heading for the future. The leading threat actions for 2018 include:
- Use of stolen credentials
- RAM scraper or malware
- Phishing (social)
- Privilege abuse of misuse
- Misdelivery or error
- Use of backdoor or C2 (hacking)
- Physical theft
- C2 (malware)
- Backdoor (malware)
- Pretexting (social)
These threat actions are not the only ones on the list, however they are posing the biggest threat in the current atmosphere. According to Verizon, “We have seven categories of threat actions that we track in our incidents. The last year has seen a decrease in malware and hacking. Phishing individuals (Social) and installing keyloggers(Malware) to steal credentials (Hacking) is still a common path even after sub setting the botnet breaches from the rest of the data.”
Biggest Threat to Your Business
This year, healthcare organizations, educational organizations and the financial services industries were all under fire. Healthcare organizations suffered more breaches than any other industry, accounting for 24 percent of all. Because of this, PII or personally identifiable information was the most common type of information acquired. The biggest threat to healthcare organizations is ransomware, which accounts for 85percent of all breaches that involve malware.
As for educational organizations, W2 scams are the most prevalent, which involve criminals posing as those needing information for W2 forms. In fact, 44 percent of education breaches involved stolen credentials and the use of backdoors into data.
Payment card skimmers are still a prevalent threat for the financial services sector. Trojans that involve banking or denial of service attacks are also big threats to the financial services industry, still the leading cause of data breaches for these institutions.
What Can Your Business Do to Prepare?
It is critical this year that your organization begins to improve its security posture, especially within the healthcare, financial services and education sectors. There are a lot of tactics your business can use to become secure including:
- Multiple authentication. For those members of your organization that use web applications or have access to databases, multiple authentication is imperative. In fact, every employee within your organization should be required to use two-factor authentication to remain secure when logging on and off the network, web applications and more.
- Implement focused or managed security. Your business will benefit from having security professionals behind your hosting that can manage, control and retain your assets. There are many options available through the cloud and data hosting. Your data will be monitored always, with availability should the network crumble.
- Have a complex security framework in place. You can only implement what you are prepared for. Having a complex security framework in place such as the HITRUST CSF will allow you to remain compliant and secure at the same time, no matter what. HITRUST is compliant with HIPAA and PCI, ISO and NIST.
Your business should remain secure, no matter the forecast. The 2018 Verizon Data Breach Investigation Report has spoken. Where do you fall? If you would like to learn more about managed security services or have questions based on the findings you see here, reach out to Onramp and their security professional services today.
Additional Resources on This Topic:
The Importance of Data Security: Understanding the True Cost
How to Mitigate and Respond to Data Breaches
2018 Threat Report: Tech Trends and Key Takeaways
How to Prevent Third Party Security Risks
This article was originally published on OnRamp.
As OnRamp’s Marketing Manager, Carolina leads the content strategy, SEO, product launch, and communication efforts at OnRamp. With experience in managed hosting, cloud computing and VoIP, she translates complex concepts into simple terms that potential customers and partners can understand and use to build compliant IT solutions.
Connect with Carolina Curby-Lucier on LinkedIn

